IIoT Security in the Omega Layer N ecosystem
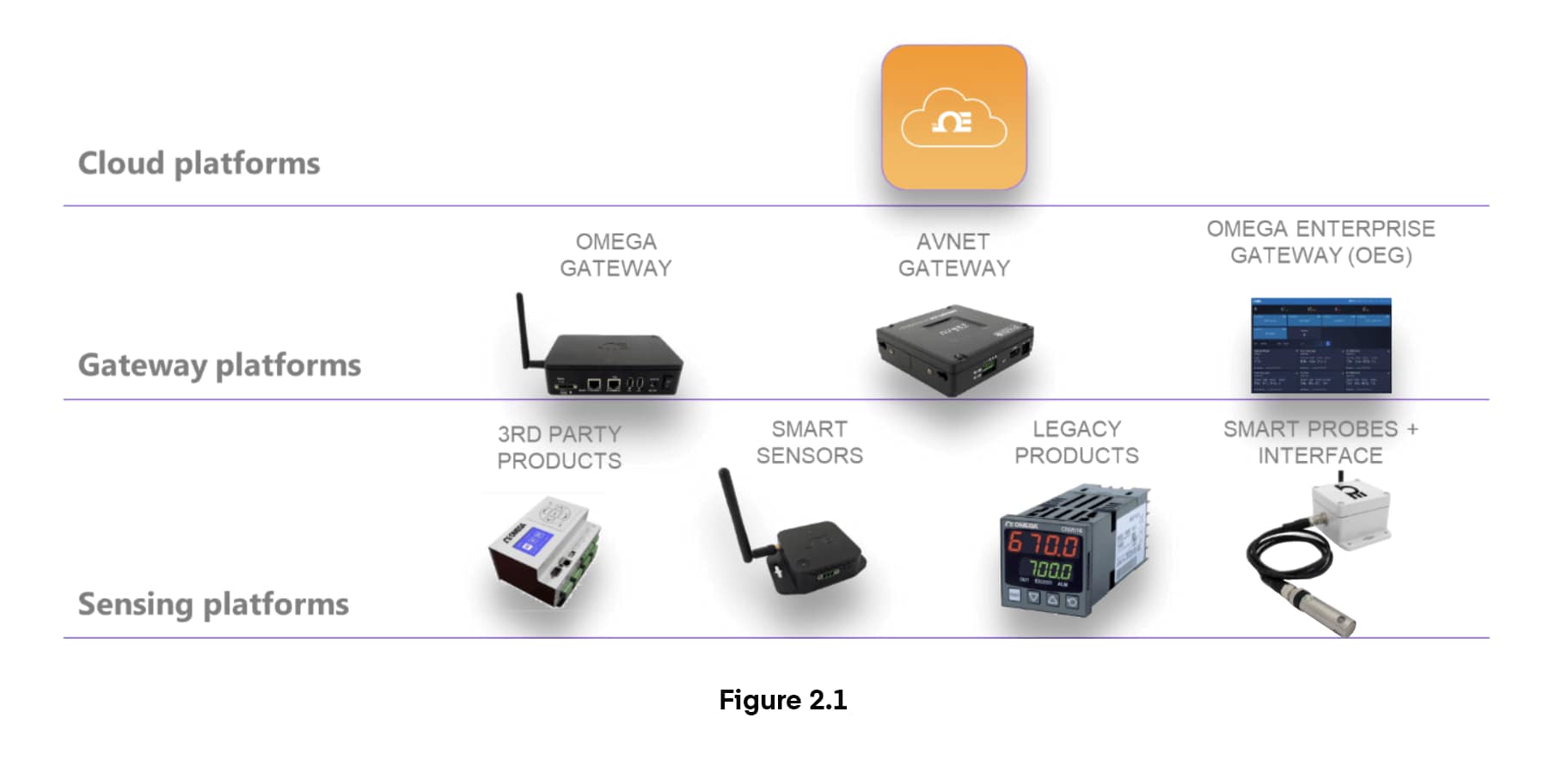
The Omega Layer N ecosystem (Figure 2.1), incorporates threat-mitigating security in every zone. The cloud layer requires user accounts passwords and a unique ID to access data and runs on Microsoft Azure which includes denial of service attack mitigation in the platform, and an IoT Hub with multiple levels of access control, authentication, and authorization. The northbound cloud/gateway connection uses the industry standard AMQP protocol on TCP/IP with Transport Layer Security (TLS), including a certificate-based authentication protocol with AES-256 encryption. Other features of the northbound protocol include:
- Separate Shared Private Keys for Gateway and Cloud with a hardware-based Trusted Platform Module (TPM) in the Gateway
- Unique challenge Codes generated by the Gateway and Cloud using shared, non-published hash function from a common challenge code that is built from shared (encrypted) Sensor Information
- Both the Gateway and Cloud validate that the authentication process has been successful
- Authentication mode on the Gateway is retained thru power cycles,
- If the Gateway enters the authentication state than ALL subsequent accesses require an authentication first or a factory reset.
- After 5 failed authentication attempts, the Gateway MUST be power cycled. Cloud access authentication will go into security challenged mode after 5 failures.
The southbound gateway-sensor connection uses the industry standard IEEE 802.15.4 AES256 encryption protocol. Features of the southbound protocol include:
- IEEE 802.15.4 ECDH (Elliptic Curve Diffie-Hellman) encrypted key agreement protocol
- Device Authentication (to avoid MiTM-- man in the middle attack)
- Link Layer Encryption AES CCM (cryptoblock cipher mode)
- Secure Over The Air (OTA) download
- On The Device (OTD) firmware boot manager with Secure Boot - verifies the authenticity of the firmware to be executed on the device upon every boot
- Sensor identity cross-checked with cloud credentials, preventing spoofing
Finally, penetration (“white hat”) testing validates that there are no vulnerabilities in the implementation. While no IIoT system guarantees immunity from every possible threat, the Layer N ecosystem does guarantee that security is incorporated as a core design feature, not as an add-on.
 CLOSE
CLOSE


 High-value assets such as aerospace systems must be monitored and protected while in transit to the final assembly location...
High-value assets such as aerospace systems must be monitored and protected while in transit to the final assembly location...
 Recording temperature in freezers is important in the storage of blood plasma, vaccines, pharmaceuticals...
Recording temperature in freezers is important in the storage of blood plasma, vaccines, pharmaceuticals...
 Understanding the principles of how they operate is vitally important when selecting a data logger for your application.
Understanding the principles of how they operate is vitally important when selecting a data logger for your application.